WPScan is (as the name suggests) for scanning wordpress websites for vulnerabilities. WPScan is both passive and aggressive depending on the setting used. In addition, it can also enumerate users and attempt brute force attacks.
For demonstration purposes, team1.pentest.id will be scanned using WPScan’s default options. Default scan uses a mix of passive and aggressive scan to detect server information, wordpress version and etc.
wpscan –url team1.pentest.id is used to initiate the scan. Sometimes, an update will be available. Updating is recommended because it may provide better result.
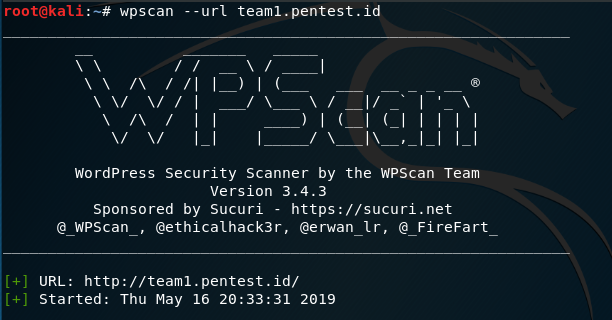
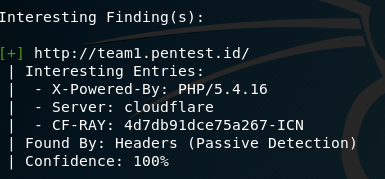
After the scan is finished, a report will be shown. The report will show confidence percentage on every finding to show how accurate or reliable that information is. There are many useful findings such as wordpress version, php version and etc that will help in penetration testing


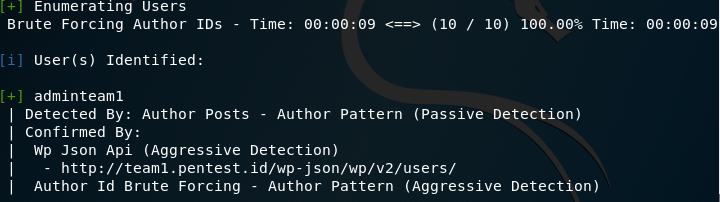
WPScan can also enumerate users. Using wpscan –url team1.pentest.id — enumerate u, wpscan will, in addition to scan, brute force author id to find possible usernames. 
In addition, wpscan can attempt a brute force attack. For example, brute forcing enumerated user @user1 using wpscan –url team1.pentest.id -U @user1 –passwords passwordlist.txt (Note: passwordlist.txt is a collection of passwords). You can also use ctrl+c to cancel the scan midway.
![]()
