February 2026 S M T W T F S 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 Archives
Disclaimer: This blog is used for educational purposes only.
Posted in Uncategorized
Leave a comment
Intelligent System Final Project Journal
Week 5
The creation of the groups were on this week. Group members: Kho Ryan Anggada and Nicolas.
links to their blog:
Nicolas – http://2101704520nicolas.blog.binusian.org/intelligent-systems/
Ryan – http://2101704672ryan.blog.binusian.org/intelligent-systems/
Posted in Uncategorized
Leave a comment
Sqlmap
Sqlmap is a powerful penetration testing tool used to detect and exploit sql injection vulnerabilities.
For demonstration, team1.pentest.id will be attacked using sqlmap
sqlmap -u “team1.pentest.id/?author=1/” 
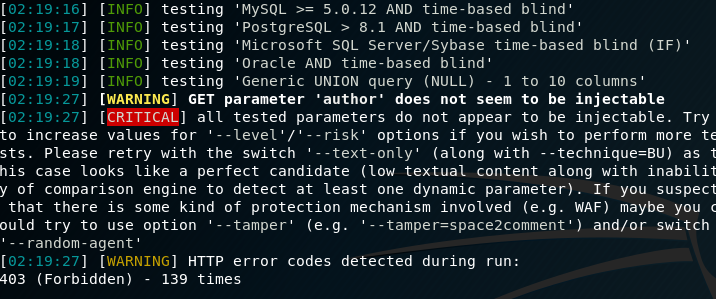
The result is that the sqlmap was unsuccessful due to error 403 forbidden.
Posted in Uncategorized
Leave a comment
Searchsploit
Searchsploit is a convenient tool used when a quick search of exploits are needed. For example if a person wants to check if there is any vulnerability in WordPress, they can use searchsploit.
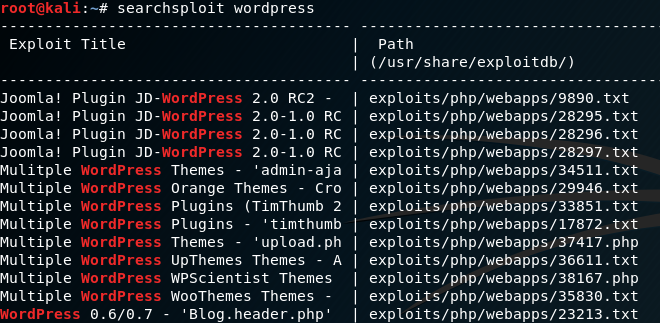
Searchsploit shows exploits for wordpress themes, plugins and etc. It also shows the version. The person also can specify his/her search so that a specific wordpress version or plugin appears.
Posted in Uncategorized
Leave a comment
Crunch
Crunch is a useful password list generator for generating password lists based on criteria.
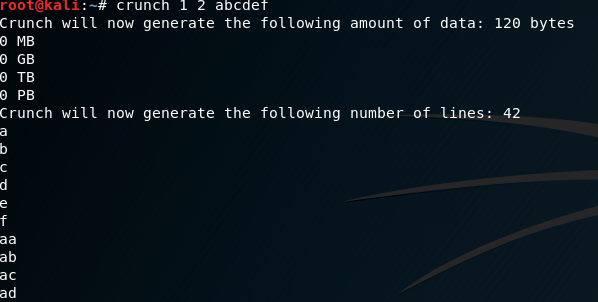
crunch min max options
where minimum is the minimum amount of characters, maximum is the maximum amount of characters and options are the characters used for crunching.
Posted in Uncategorized
Leave a comment
Whois
Whois is a convenient tool used to search domain information.
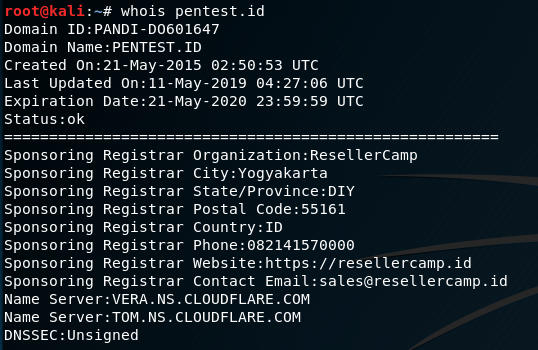
This tool shows registrar info, name server, expiration date and etc.
Posted in Uncategorized
Leave a comment
John The Ripper
John the ripper is a powerful tool used for offline cracking tool. It can autodetect a lot of hashes such as FreeBSD MD5-based and etc.
For demonstration, the shadow file in /etc/shadow/ will be cracked in the VM.
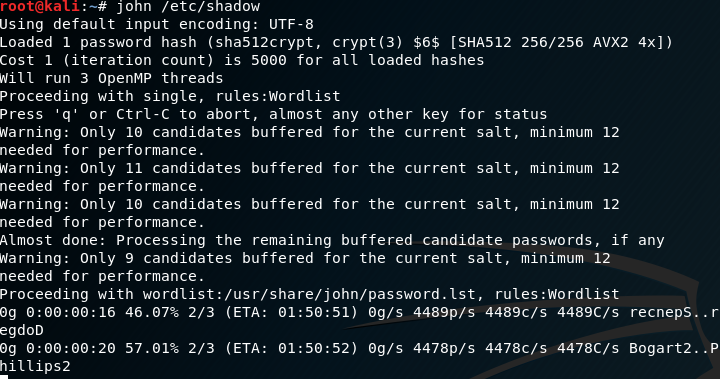
From this picture, we can see that it auto loads the hash.
It also has the unshadow function which combines the passwd file with the shadow file.
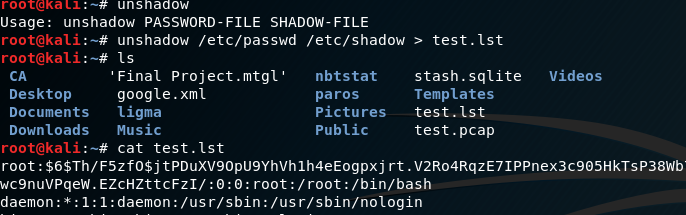
Posted in Uncategorized
Leave a comment
Nikto Website Scanner
Nikto is a website scanning tool designed not for stealth, but for quickest result. Nikto has many features such as checking for outdated software versions (PHP, apache, etc), checking for vulnerability and etc.
Posted in Uncategorized
Leave a comment
Vulnerability Exploitation Using Metasploit
The Metasploit framework is a very powerful tool capable of information gathering, vulnerability analysis, exploit vulnerabilities and etc. For a full tutorial, visit https://www.offensive-security.com/metasploit-unleashed/.
Posted in Uncategorized
Leave a comment
Dirb Web Content Scanner
DIRB is a web content scanner used for scanning both hidden and non hidden web objects. It does a dictionary based attack against a web server and checks every response given.
Posted in Uncategorized
Leave a comment
Nmap
Nmap is a network mapping tool used for network discovery. Nmap can get information such as open ports, OS, version and etc. Nmap has a lot of options such as syn scan, udp scan and etc.
Posted in Uncategorized
Leave a comment
